How to encrypt your internet traffic
There are many reasons why you might want to encrypt your internet traffic. You might want to conceal your internet browsing from ISP tracking, for example, or perhaps you’d like to improve your security on the internet and shield your information from cybercriminals. Whatever your motivation, we’ll explain what encryption is, why it’s important, and how to do it .
A guide to internet encryption
Why is internet encryption vital?
Encryption of internet traffic has become a critical need for many users, in light of the recent information maintenance laws around the globe that have allowed the ISP to record and maintain clients’ information. Free connectivity and openness is the right of internet users , and yet there are numerous countries and organizations that would limit this freedom by tracking users’ activity and censoring access to content. In such cases, internet traffic privacy is essential.
Encrypting your internet traffic gives you the ability to conceal your online activity from the checking of ISP, ensuring that delicate information like passwords and Visa points of interest are not passed to ISPs and potentially from there to governments or other organizations. This is one reason it is so vital to encrypt your internet traffic.
There are numerous approaches to encrypt internet traffic: VPNs, https, interfacing with Tor programs, utilizing encrypted messaging applications and browser extensions . Let’s go through each of these now.
Virtual private network – VPN
As the name suggests, a virtual private network , or VPN , is a private and encrypted route to connect over the internet to another private system. It requires initial setup and validation in order to work, and after that, it encrypts all the activity between the third-party servers. Using an encrypted VPN tunnel enables the user to browse the web using a masked IP address that seems to be coming from the VPN server, making it difficult to distinguish the user.
Your internet traffic can be seen, adjusted, and logged by the VPN services themselves, however. Though many VPN services guarantee that they don’t keep logs of your internet traffic and utilize extra security defensive measures, this is a difficult claim to verify. And in fact, a recent investigation revealed that many VPN apps for Android contain malware designed to track users. So do your homework before choosing a VPN provider .
google_ad_client = "ca-pub-8132844949421936"; var google_ad_slot = '9677578764'; if (window.innerWidth <= 470) { google_ad_width = 300; google_ad_height = 50; } else if (window.innerWidth < 1360) { google_ad_width = 468; google_ad_height = 60; } else { google_ad_width = 728; google_ad_height = 90; }
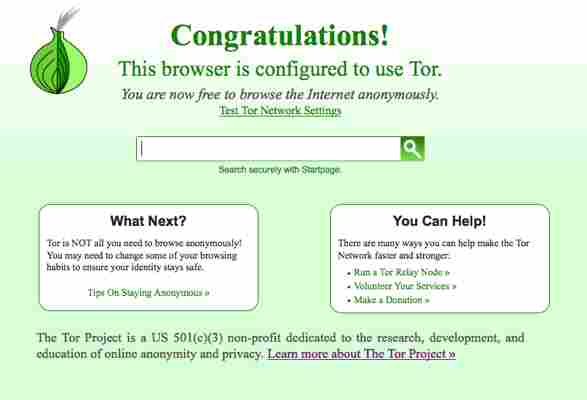
Tor – the onion router
Tor is a distributed relay system that routes the movement of internet traffic by encrypting the IP address at each bounce point in the relay. At each relay, only the last and next IP station are accessible to enable routing.
Tor is one of the most secure browsers in the world since it conceals your activity from the ISPs. When you are are using a Tor browser, your ISP will just see that you are associated with a Tor system, but it can’t determine your destination.
Tor can dodge recognition from all but the most capable state-controlled monitoring machines. Even the NSA has some difficulty breaking Tor. So it’s a good solution to protect your browsing for most activities, though if an organization needs to invest the energy and assets to watch you, they can and will.
Browser extensions
Browser extensions are also useful security tools. Extensions are available that let you control your internet traffic, block ads on the websites that you visit, and kill the cookies and traces that could share your information without your knowledge. This does not imply that you can completely depend on these extensions to do everything for you, but they are good to have in your toolbox.

Even if you do use browser extensions, you should check to see if your DNS has a leak. DNS leaks can be a big security risk, as it might give your internet traffic data to your ISP. You can use DNS leak test to determine whether or not this is an issue with your device.
Encrypted chat apps
Many modern chat applications are encrypted using a method called end-to-end encryption , which ensures that your chats are secure from monitoring. The structures of end-to-end encryption make it virtually impossible to unravel the data being passed. For example, connections that use end-to-end encryption can’t pass on their customers’ messages to third-parties. If you’re using a chat client and you are concerned about privacy, make sure that your messages are getting encrypted.
Encrypting your internet traffic is fundamental, especially in an era of government monitoring and the rising danger from cybercriminals. Using these simple strategies will keep prying eyes from your data and won’t require much work from you.